Understanding Key Networking Protocols - 90 Days of DevOps Challenge
In today’s interconnected world, networking protocols are the unsung heroes that keep the internet running smoothly. Whether you’re browsing a website, sending an email, or streaming a video, these protocols work behind the scenes to ensure seamless communication between devices. In this blog, we’ll explore some of the most important networking protocols—RARP, ARP, ICMP, HTTP, HTTPS, FTP, and DNS—and explain how they work using real-world analogies to make them easy to understand.
1. ARP (Address Resolution Protocol)
ARP, or Address Resolution Protocol, is used to find the MAC address of a device when its IP address is known. It helps devices on the same local network communicate by mapping IP addresses to physical hardware addresses.

(image source : fortinet.com/resources/cyberglossary/what-i..)
How Does ARP Work?
When a device wants to send data to another device on the same network, it broadcasts an ARP request: “Who has this IP address? Tell me your MAC address.” The device with that IP address responds with its MAC address.
Imagine you’re at a party, and you know someone’s name (IP address) but not their face (MAC address). You shout, “Hey, John, where are you?” John responds, “I’m over here!” Now you know where to find him.
2. RARP (Reverse Address Resolution Protocol)
RARP, or Reverse Address Resolution Protocol, is used to find the IP address of a device when only its MAC address (hardware address) is known. It’s the reverse of ARP and was commonly used in older systems or diskless workstations.
How Does RARP Work?
A device sends a broadcast message saying, “Hey, I have this MAC address. What’s my IP address?” The RARP server responds with the corresponding IP address.
For example, you have a flight number (MAC address) but don’t know the airline or departure/arrival details (IP address). You contact the airport, and they use the flight number to retrieve the flight’s details (IP address).
Why is RARP Rarely Used Today?
RARP has been replaced by more advanced protocols like DHCP (Dynamic Host Configuration Protocol), which can assign IP addresses dynamically and provide additional configuration details.
3. ICMP (Internet Control Message Protocol)
ICMP, or Internet Control Message Protocol, is used for error reporting and diagnostic purposes. It helps devices check connectivity, troubleshoot network issues, and report errors like unreachable hosts or network congestion.

(image source : cloudns.net/blog/what-is-icmp-internet-serv..)
How Does ICMP Work?
ICMP messages are sent between devices to indicate issues or test connectivity. For example, when you ping a server, your computer sends an ICMP Echo Request, and the server responds with an ICMP Echo Reply.
Think of ICMP as a network’s “health check” system. For example, if you’re driving and see a “Road Closed” sign (ICMP error message), you know there’s an issue ahead and need to take a detour.
4. HTTP (Hypertext Transfer Protocol)
HTTP, or Hypertext Transfer Protocol, is the protocol used for transferring web pages and other content over the internet. It’s the foundation of data communication on the World Wide Web.

(image source : bunny.net/academy/http/what-is-http-hyperte..)
How Does HTTP Work?
When you type a URL (e.g., http://example.com) into your browser, it sends an HTTP request to the server. The server responds with the requested webpage or resource.
Think of HTTP as a librarian who fetches books (web pages) for you when you ask for them. You request a book (type a URL), and the librarian brings it to you.
5. HTTPS (Hypertext Transfer Protocol Secure)
HTTPS is the secure version of HTTP. It encrypts the data being transferred between your browser and the server to protect it from eavesdropping or tampering.

(image source : geeksforgeeks.org/explain-working-of-https)
How Does HTTPS Work?
HTTPS uses TLS/SSL encryption to secure the data. When you visit an HTTPS website, your browser and the server establish a secure connection using a process called the TLS handshake.
Think of HTTPS as a secure courier service. Instead of sending a letter (data) in an open envelope (HTTP), you seal it in a tamper-proof package (encryption) so no one can read or alter it during transit.
6. FTP (File Transfer Protocol)
FTP, or File Transfer Protocol, is used to transfer files between a client and a server over a network. It’s commonly used for uploading files to a website or downloading large files.
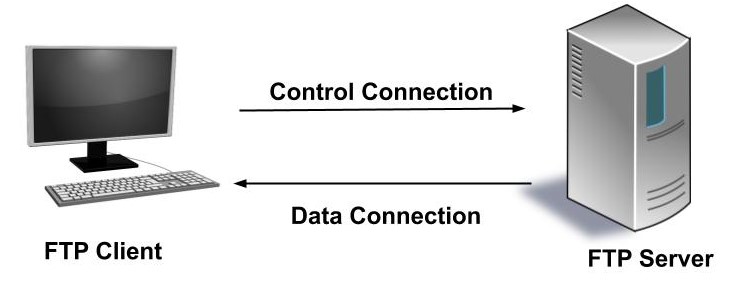
(image source : afteracademy.com/blog/what-is-ftp-and-how-d..)
How Does FTP Work?
FTP uses two channels:
Control channel: Manages the connection and sends commands (e.g., login, list files).
Data channel: Transfers the actual files.
Think of FTP as a file delivery service. You tell the delivery person (FTP client) what files to pick up or drop off, and they handle the transfer between your home (client) and the warehouse (server).
7. DNS (Domain Name System)
DNS, or Domain Name System, translates human-readable domain names (e.g., google.com) into IP addresses (e.g., 142.250.190.14) that computers use to locate each other on the internet.

(image source : geeksforgeeks.org/working-of-domain-name-sy..)
How Does DNS Work?
When you type a URL into your browser, it sends a DNS query to a DNS server. The DNS server responds with the corresponding IP address, allowing your browser to connect to the website.
Think of DNS as a phone book for the internet. When you want to call someone (connect to a website), you look up their name (domain) in the phone book (DNS) to find their phone number (IP address).
Table: Protocols, Their Uses, and Examples
| Protocol | Purpose | Examples |
| ARP | Finds the MAC address of a device when its IP address is known. | Shouting, “Hey, John, where are you?” at a party to find someone’s location. |
| RARP | Finds the IP address of a device when only its MAC address is known. | Using the flight number to find the flight’s details. |
| ICMP | Used for error reporting and diagnostics (e.g., ping and traceroute). | A “Road Closed” sign on a highway that helps you detect and avoid network issues. |
| HTTP | Transfers web pages and content over the internet. | A librarian fetching books (web pages) for you when you request them. |
| HTTPS | Securely transfers web pages and content using encryption. | A secure courier delivering a tamper-proof package (encrypted data) to ensure privacy and security. |
| FTP | Transfers files between a client and a server. | A file delivery service that picks up and drops off files between your home (client) and a warehouse (server). |
| DNS | Translates domain names (e.g., google.com) into IP addresses (e.g., 142.250.190.14). | A phone book that looks up a name (domain) and gives you the phone number (IP address). |
Conclusion
Networking protocols like RARP, ARP, ICMP, HTTP, HTTPS, FTP, and DNS are the backbone of the internet. They ensure that devices can communicate, data can be transferred securely, and users can access websites and services effortlessly.
If you like reading articles related to DevOps, Cloud and tech then please make sure to follow me on hashnode.